# shiro
# 1.Apache Shiro Architecture
Apache Shiro的设计目标是通过直观和易用来简化应用程序安全性。 Shiro的核心设计模拟了大多数人对应用程序安全性的看法 -在某人(或某事)与应用程序交互的环境中。
Apache Shiro’s design goals are to simplify application security by being intuitive and easy to use. Shiro’s core design models how most people think about application security - in the context of someone (or something) interacting with an application.
软件应用程序通常基于用户故事设计。也就是说,您通常会根据用户(或应该)与软件交互的方式设计用户界面或服务API。例如,您可能会说,“如果用户与我的应用程序交互,则会向他们显示一个按钮,他们可以单击该按钮查看其帐户信息。如果他们没有登录,我会显示一个注册按钮。“
Software applications are usually designed based on user stories. That is, you’ll often design user interfaces or service APIs based on how a user would (or should) interact with the software. For example, you might say, “If the user interacting with my application is logged in, I will show them a button they can click to view their account information. If they are not logged in, I will show a sign-up button.”
此示例语句指示应用程序主要是为满足用户要求和需求而编写的。即使“用户”是另一个软件系统而不是人类,您仍然会编写代码以反映基于当前与您的软件交互的人(或什么)的行为。
This example statement indicates that applications are largely written to satisfy user requirements and needs. Even if the ‘user’ is another software system and not a human being, you still write code to reflect behavior based on who (or what) is currently interacting with your software.
Shiro在自己的设计中反映了这些概念。通过匹配软件开发人员已经很直观的内容,Apache Shiro在几乎任何应用程序中都保持直观且易于使用。
Shiro reflects these concepts in its own design. By matching what is already intuitive for software developers, Apache Shiro remains intuitive and easy to use in practically any application.
# 1.1.High-Level Overview
在最高概念层面,Shiro的架构有3个主要概念:主题,SecurityManager和领域。下图是这些组件如何交互的高级概述,我们将在下面介绍每个概念:
At the highest conceptual level, Shiro’s architecture has 3 primary concepts: the Subject, SecurityManager and Realms. The following diagram is a high-level overview of how these components interact, and we’ll cover each concept below:
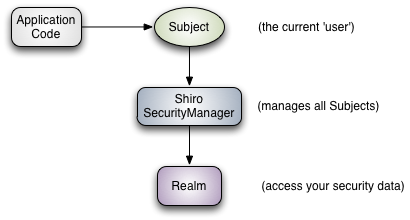
Subject:正如我们在教程中提到的,Subject本质上是当前正在执行的用户的特定于安全性的“视图”。虽然“用户”这个词通常意味着一个人,但主体可以是一个人,但它也可以代表第三方服务,守护进程帐户,cron作业或任何类似的东西 -基本上是当前与软件交互的任何东西。
Subject: As we’ve mentioned in our Tutorial, the Subject is essentially a security specific ‘view’ of the the currently executing user. Whereas the word ‘User’ often implies a human being, a Subject can be a person, but it could also represent a 3rd-party service, daemon account, cron job, or anything similar - basically anything that is currently interacting with the software.
Subject实例都绑定到(并要求)SecurityManager。当您与Subject进行交互时,这些交互会转换为与SecurityManager特定于主题的交互。
Subject instances are all bound to (and require) a SecurityManager. When you interact with a Subject, those interactions translate to subject-specific interactions with the SecurityManager.
SecurityManager:SecurityManager是Shiro架构的核心,它充当一种“’umbrella’”对象,协调其内部安全组件,共同形成一个对象图。但是,一旦为应用程序配置了SecurityManager及其内部对象图,通常就会将其保留,应用程序开发人员几乎将所有时间花在Subject API上。
SecurityManager: The SecurityManager is the heart of Shiro’s architecture and acts as a sort of ’umbrella’ object that coordinates its internal security components that together form an object graph. However, once the SecurityManager and its internal object graph is configured for an application, it is usually left alone and application developers spend almost all of their time with the Subject API.
我们稍后会详细讨论SecurityManager,但重要的是要意识到当你与Subject交互时,它实际上是幕后的SecurityManager,它可以完成任何Subject安全操作的繁重任务。这反映在上面的基本流程图中。
We will talk about the SecurityManager in detail later on, but it is important to realize that when you interact with a Subject, it is really the SecurityManager behind the scenes that does all the heavy lifting for any Subject security operation. This is reflected in the basic flow diagram above.
Realms:领域充当Shiro与应用程序安全数据之间的“桥梁”或“连接器”。当实际与安全相关数据(如用户帐户)进行交互以执行身份验证(登录)和授权(访问控制)时,Shiro会从为应用程序配置的一个或多个领域中查找许多这些内容。
Realms: Realms act as the ‘bridge’ or ‘connector’ between Shiro and your application’s security data. When it comes time to actually interact with security-related data like user accounts to perform authentication (login) and authorization (access control), Shiro looks up many of these things from one or more Realms configured for an application.
从这个意义上讲,Realm本质上是一个特定于安全性的DAO:它封装了数据源的连接细节,并根据需要使相关数据可用于Shiro。配置Shiro时,必须至少指定一个Realm用于身份验证和/或授权。 SecurityManager可以配置多个领域,但至少需要一个领域。
In this sense a Realm is essentially a security-specific DAO: it encapsulates connection details for data sources and makes the associated data available to Shiro as needed. When configuring Shiro, you must specify at least one Realm to use for authentication and/or authorization. The SecurityManager may be configured with multiple Realms, but at least one is required.
Shiro提供了开箱即用的Realms,可以连接到许多安全数据源(也称为目录),如LDAP,关系数据库(JDBC),文本配置源(如INI和属性文件等)。如果默认域不符合您的需要,您可以插入自己的Realm实现来表示自定义数据源。
Shiro provides out-of-the-box Realms to connect to a number of security data sources (aka directories) such as LDAP, relational databases (JDBC), text configuration sources like INI and properties files, and more. You can plug-in your own Realm implementations to represent custom data sources if the default Realms do not meet your needs.
与其他内部组件一样,Shiro SecurityManager管理如何使用Realms获取要表示为Subject实例的安全性和身份数据。
Like other internal components, the Shiro SecurityManager manages how Realms are used to acquire security and identity data to be represented as Subject instances.
# 2.Detailed Architecture
The following diagram shows Shiro’s core architectural concepts followed by short summaries of each:

Subject (org.apache.shiro.subject.Subject)
A security-specific ‘view’ of the entity (user, 3rd-party service, cron job, etc) currently interacting with the software.SecurityManager (org.apache.shiro.mgt.SecurityManager)
As mentioned above, the SecurityManager is the heart of Shiro’s architecture. It is mostly an ‘umbrella’ object that coordinates its managed components to ensure they work smoothly together. It also manages Shiro’s view of every application user, so it knows how to perform security operations per user.Authenticator (org.apache.shiro.authc.Authenticator)
The Authenticator is the component that is responsible for executing and reacting to authentication (log-in) attempts by users. When a user tries to log-in, that logic is executed by the Authenticator. The Authenticator knows how to coordinate with one or more Realms that store relevant user/account information. The data obtained from these Realms is used to verify the user’s identity to guarantee the user really is who they say they are.- Authentication Strategy (org.apache.shiro.authc.pam.AuthenticationStrategy)
If more than one Realm is configured, the AuthenticationStrategy will coordinate the Realms to determine the conditions under which an authentication attempt succeeds or fails (for example, if one realm succeeds but others fail, is the attempt successful? Must all realms succeed? Only the first?).
- Authentication Strategy (org.apache.shiro.authc.pam.AuthenticationStrategy)
Authorizer (org.apache.shiro.authz.Authorizer)
The Authorizer is the component responsible determining users’ access control in the application. It is the mechanism that ultimately says if a user is allowed to do something or not. Like the Authenticator, the Authorizer also knows how to coordinate with multiple back-end data sources to access role and permission information. The Authorizer uses this information to determine exactly if a user is allowed to perform a given action.SessionManager (org.apache.shiro.session.mgt.SessionManager)
The SessionManager knows how to create and manage user Session lifecycles to provide a robust Session experience for users in all environments. This is a unique feature in the world of security frameworks - Shiro has the ability to natively manage user Sessions in any environment, even if there is no Web/Servlet or EJB container available. By default, Shiro will use an existing session mechanism if available, (e.g. Servlet Container), but if there isn’t one, such as in a standalone application or non-web environment, it will use its built-in enterprise session management to offer the same programming experience. The SessionDAO exists to allow any datasource to be used to persist sessions.- SessionDAO (org.apache.shiro.session.mgt.eis.SessionDAO)
The SessionDAO performs Session persistence (CRUD) operations on behalf of the SessionManager. This allows any data store to be plugged in to the Session Management infrastructure.
- SessionDAO (org.apache.shiro.session.mgt.eis.SessionDAO)
CacheManager (org.apache.shiro.cache.CacheManager)
The CacheManager creates and manages Cache instance lifecycles used by other Shiro components. Because Shiro can access many back-end data sources for authentication, authorization and session management, caching has always been a first-class architectural feature in the framework to improve performance while using these data sources. Any of the modern open-source and/or enterprise caching products can be plugged in to Shiro to provide a fast and efficient user-experience.Cryptography (org.apache.shiro.crypto.*)
Cryptography is a natural addition to an enterprise security framework. Shiro’s crypto package contains easy-to-use and understand representations of crytographic Ciphers, Hashes (aka digests) and different codec implementations. All of the classes in this package are carefully designed to be very easy to use and easy to understand. Anyone who has used Java’s native cryptography support knows it can be a challenging animal to tame. Shiro’s crypto APIs simplify the complicated Java mechanisms and make cryptography easy to use for normal mortal human beings.Realms (org.apache.shiro.realm.Realm)
As mentioned above, Realms act as the ‘bridge’ or ‘connector’ between Shiro and your application’s security data. When it comes time to actually interact with security-related data like user accounts to perform authentication (login) and authorization (access control), Shiro looks up many of these things from one or more Realms configured for an application. You can configure as many Realms as you need (usually one per data source) and Shiro will coordinate with them as necessary for both authentication and authorization.
